With the advent of the fully automated and free of cost certificate authorities Let’s Encrypt and StartCom there is no doubt that the future of CAs are changing.
Tag Archives: https
Let’s Encrypt for Nginx
Let’s install an SSL-certificate from Let’s Encrypt for Nginx.
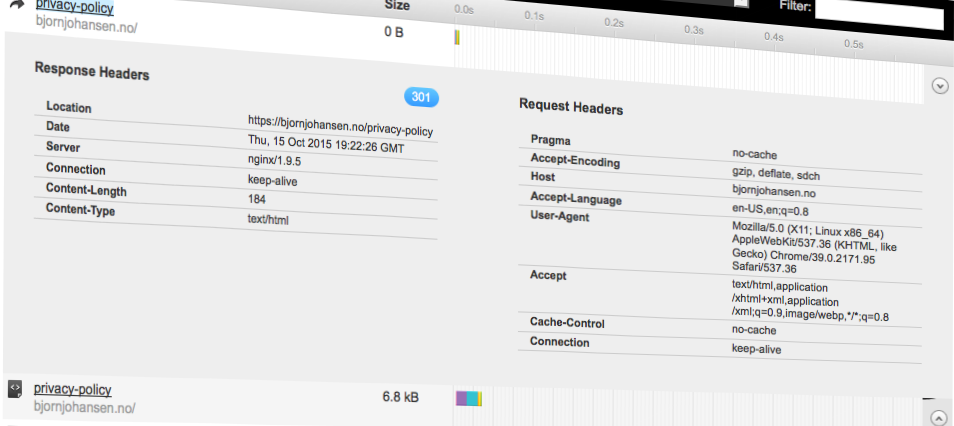
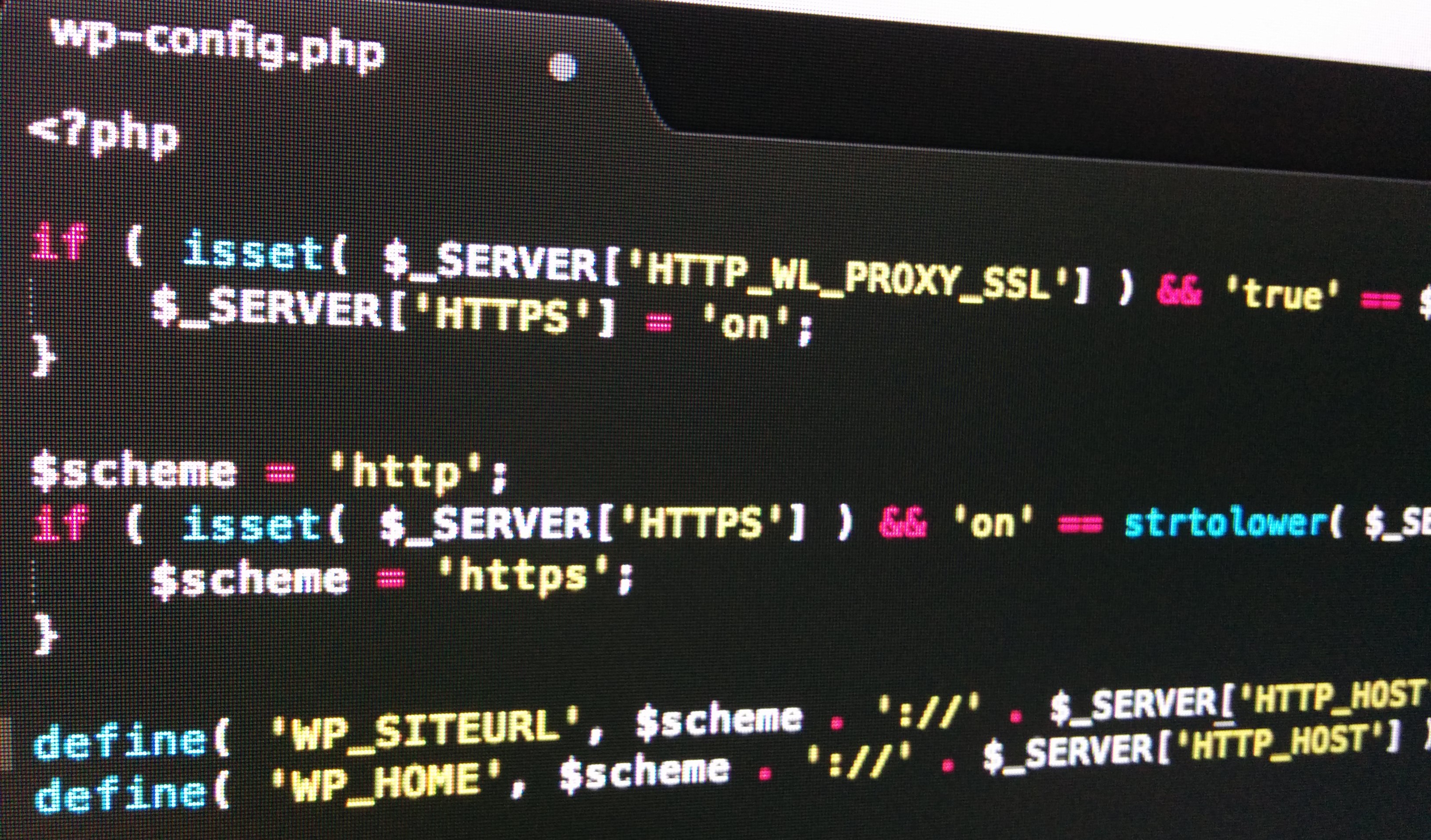
Redirect all HTTP requests to HTTPS with Nginx
All login credentials transferred over plain HTTP can easily be sniffed by an MITM attacker, but is is not enough to encrypt the login forms. If you are visiting plain HTTP pages while logged in, your session can be hijacked, and not even two-factor authentication will protect you. To protect all info sent between your visitors – which includes you – and your web server, we will redirect all requests that are coming over plain HTTP to the HTTPS equivalent.
Continue reading “Redirect all HTTP requests to HTTPS with Nginx”
WordPress behind Big-IP
To be honest, I don’t exactly know too much about Big-IP, but I’ve come across someone who use it. They terminate HTTPS in Big-IP and WordPress runs on plain HTTP on port 80 on the backend nodes. By default, this makes WordPress confused, so you can’t login to the WordPress dashboard.Continue reading “WordPress behind Big-IP”
HTTP Public Key Pinning (HPKP)
Using HTTPS helps preventing someone from snooping your username/password or hijacking your sessions. Using HSTS makes sure the connection stays on HTTPS, even if a MITM tries to redirect you to the plain HTTP version of a web site. But it is easier than you might think for a MITM to use a rogue certificate, making you believe everything is fine. HTTP Public Key Pinning (HPKP) helps the browser check that everything actually is fine.Continue reading “HTTP Public Key Pinning (HPKP)”
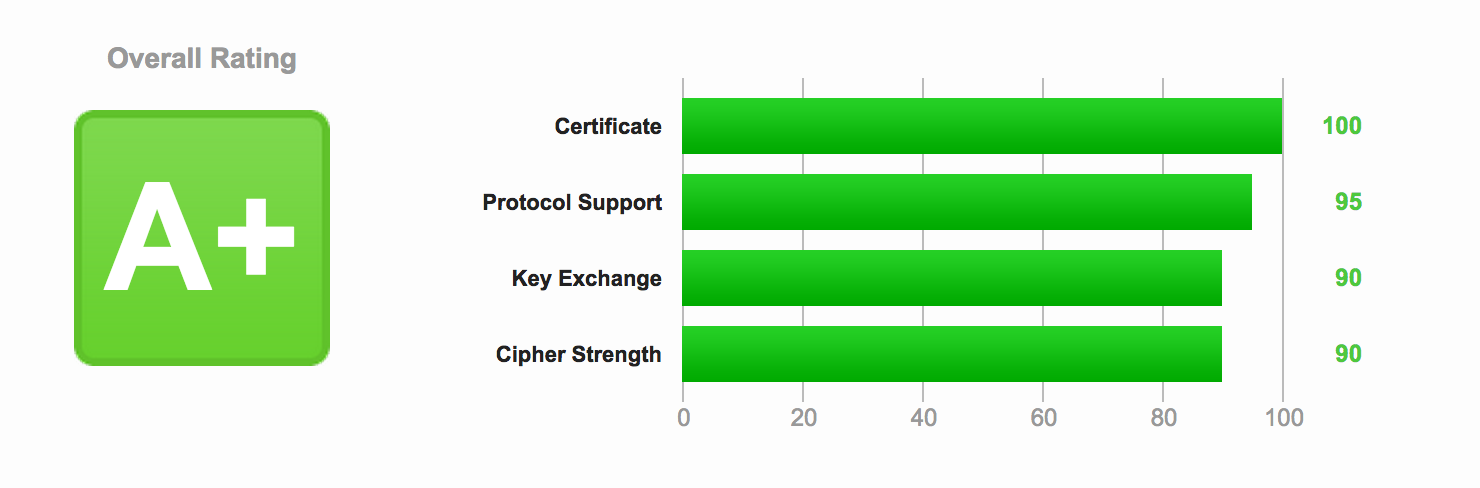
Optimizing HTTPS on Nginx
Now that you have secured Nginx with HTTPS and enabled SPDY enabled HTTP/2, it’s time to improve both the security and the performance of the server.Continue reading “Optimizing HTTPS on Nginx”
Securing Nginx with HTTPS
 Adding a certificate and using the HTTPS protocol is a good improvement to the security in the communication between the browser and the server, and should be in place on all sites that have a user login. Contrary to what many (older) guides say, it doesn’t add much load on your server and is fairy easy and cheap to set up right.Continue reading “Securing Nginx with HTTPS”
Adding a certificate and using the HTTPS protocol is a good improvement to the security in the communication between the browser and the server, and should be in place on all sites that have a user login. Contrary to what many (older) guides say, it doesn’t add much load on your server and is fairy easy and cheap to set up right.Continue reading “Securing Nginx with HTTPS”